Did you know your USB Battery Bank is cheating on you? Do you know what a USB Battery Bank is? Let’s cover the latter question first.
What Is A USB Battery Bank?
Most of us these days have lots of tech devices and all those tech devices LOVE to eat power. Many of them have rechargeable batteries, and, in many cases, if you don’t attach them to a power cord every few hours, you’ll be getting a blinking and / or beeping indicator that the battery is almost dead. Many of these devices now have a micro USB power plug, and thus can be charged from the USB port on a PC (if they only need 500 mA of current) or from a USB power adapter like you can plug into your house electrical outlet or your car’s cigarette lighter. The latter two devices can usually supply 1 A of current or even 2+ A of current for larger devices.
But, what if you’re not near a power outlet? What if you’re on a trip? What if you’re roaming around in your car without a power adapter? What if you’re walking down the street and your device’s battery is dying?
This is where the USB Battery Bank comes in. These go by different names including: USB Battery Bank, USB Battery Pack, USB Power Bank, USB Power Pack, and various other permutations. The concept is simple. The manufacturers take a rechargeable battery, some control electronics, some status indicators, and a few buttons and connectors and package all that up in a portable case. When it’s done, you have a portable battery that you can take with you to pump up the charge of your other devices when you need to, within the capacity limits of the portable battery. Most smaller battery banks charge from a USB plug. Some larger ones charge from AC power. The output is a USB port with an output voltage of 5.0 V.
So, you charge up your USB Battery Bank and take it with you to your car or on your walk. When your cell phone with its big bright screen starts getting low on charge, you connect the USB Battery Bank to the phone and charge the phone’s battery. Life is good.
Your USB Battery Bank Is Cheating On You
Now, back to my first question. Did you know your USB Battery Bank is cheating on you? No, it’s not helping your spouse arrange secret dates. IT, itself, is cheating on you. It’s deceiving you, and you don’t even know it. It starts deceiving you the moment you look at it in a store, in a catalog, or online.
This applies to USB Battery Banks in travel routers and similar devices as well as stand alone devices of almost any brand. If you buy one of these USB battery banks, of almost any brand, you are automatically being snookered. That’s because the entire industry uses deceptive labeling and is misleading people about the battery bank output capacity. The unit I bought says it has a 6000 mAH capacity. Well, I NATURALLY assumed, as most consumers would, that I could get 6000 mAH from the OUTPUT port. So, you’d think you could charge a 2000 mAH device about 3 times. Well, you CAN’T. I actually requested a replacement device because I wasn’t getting enough charge from the output. That was before I learned what I’m about to share.
Basic Electronics
Battery specs involve 3 basic parameters: nominal (average) voltage, current capacity over time, and total power capacity.
A word about prefixes. In the context of these discussions, the prefix “m” means the metric prefix of milli, which means 1/1000. So, a milliamp (or mA) is 1/1000 of an Amp.
https://en.wikipedia.org/wiki/Metric_prefix
We can make some general analogies between electricity in a wire and water in a container or hose.
Current, measured in Amps (or fractions of it), is a FLOW RATE of electricity. It is roughly analogous to gallons per minute of water.
https://en.wikipedia.org/wiki/Electric_current
Voltage, measured in Volts (or fractions of it), is essentially ELECTRICAL PRESSURE. It is roughly analogous to pounds per square inch of water pressure. Note that I said ROUGHLY analogous. The important thing to know is, the more pressure, the more quickly the current wants to flow and the more it wants to break through barriers.
https://en.wikipedia.org/wiki/Voltage
Finally, power is the combination of voltage and current and represents the ability to do work at a certain rate. The term horsepower literally is derived from the rate at which a strong healthy horse can do work.
Electrical power is measured in Watts (or fractions of it).
The analogy to water is say you have a tank of water under pressure. You let the water come out of a pipe and turn a turbine. The more pressure, the more flow, and the more power the water has and the more work the turbine does, because of both the pressure and the flow.
https://en.wikipedia.org/wiki/Electric_power
Battery Ratings
Batteries are rated by 3 primary factors:
voltage output – The average voltage that the battery maintains while its output is usable.
mAH – milliamp-hours – While the battery output varies continuously, if it can provide, on average, 1 mA of current for 1 hour, that is 1 mAH. This measures the total amount of electricity it can provide.
mWH – milliwatt-hours – While the battery output varies continuously, if it can provide, on average, 1 mW of power for 1 hour, that is 1 mWH. This measures the total amount of power it can provide.
How The USB Battery Bank Deceives You
As I mentioned before, I and the average consumer would assume that if the box says 6000 mAH, that the battery BANK, the device I’m holding in my hand, would output that much current on the OUTPUT port AT the OUTPUT VOLTAGE, which, for USB, is 5.0 V. This is not the case.
The problem is that the rating on the box is (in almost all cases) the rating of the BATTERY, not the BATTERY BANK!
If the battery bank has a Lithium Ion battery inside, which many do; that battery would have an output voltage of 3.6 V. Little did you or I know, but the rating on the box is the rating of THAT battery at THAT voltage. So, it can output 6000 mAH in our example AT 3.6 V.
You can calculate DC (battery) power by multiplying current times voltage, so:
6000 mAH x 3.6 V = 21,600 mWH
That is the total power the battery can supply. HOWEVER, we have to divide by 5 V if we want to find the mAH at the USB output.
21,600 mWH / 5 V = 4320 mAH @ 5.0 V
This is the current capacity that should THEORETICALLY come out of the USB port. BUT, that’s not the end of the story.
Between the battery and the USB output port is a device called a “boost converter”. This device converts the 3.6 V coming from the battery to the 5.0 V at the USB output port. This device can be very efficient or very inefficient. I’m going to use some pretty much worst case numbers here but these correlate well to my testing on the battery bank I have. Assume this device is 75% efficient. That means we will lose 25% of our theoretical output. So:
4320 mAH x 75% = 3240 mAH @ the USB OUTPUT port @ 5.0 V
So, the bottom line is, with a 6000 mAH USB Battery Bank, you may only get 3240 mAH out of the USB port to charge your devices.
You actually get about 1/2 of the capacity FROM THE USB OUTPUT port versus what’s stated on the box in almost all cases.
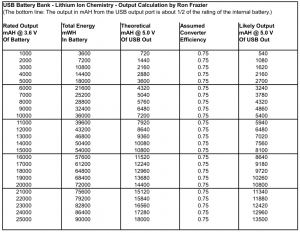
I’ve created a chart which shows about how much energy you can expect to actually get out with different USB Battery Bank sizes.
Here’s a link to the chart in a PDF file:
https://techstarship.com/wp-content/uploads/2016/02/usb-battery-banks.pdf
How to read the chart:
Column 1 – Shows the battery bank rating you might read on the packaging.
Column 2 – Shows the total power the battery can supply.
Column 3 – Shows the theoretical current capacity available at the USB output port @ 5.0 V.
Column 4 – Shows the assumed boost converter efficiency.
Column 5 – Shows the likely current capacity available at the USB output port @ 5.0 V.
Additional Info And Resources
You can use the following device to actually measure what’s coming from the USB port.
http://www.amazon.com/gp/product/B00S2HJAUE
Also, be aware that normal USB charging cables are not rated for high currents. They are typically designed for .5 A or 500 mA. You can use the following cable to get better results with higher charging currents, assuming your battery or power supply is capable of that. Note, however, that these cables are only for charging. They do not transmit data. This can be a good thing if you want to protect your devices from being infected with a virus coming from the charger. (YES, that can happen.) Not sure if these work with Apple devices or not.
http://www.amazon.com/gp/product/B0088HTYUE
Here are some other blog posts on the subject.:
http://blog.banggood.com/the-secret-marketing-trick-behind-powerbank-capacity-29982.html
http://thewirecutter.com/reviews/best-usb-battery-packs/
Enjoy. As always, Let The Buyer Beware!
Ron