Posted: February 18, 2016 at 12:32 AM EST
Updated: June 9th, 2016.
Updated: March 6th, 2017 at 02:35 PM EST
—Added this article to some other categories. Added RSS links at the bottom.
One of the things on many people’s wish list is an IOT item of one kind or another. Before I go on, I should define that jargon word. IOT stands for Internet Of Things.
https://en.wikipedia.org/wiki/Internet_of_Things
For the purposes of this discussion, I’m going to consider an IOT thing to be any network connected device that is not a traditional computer, tablet, or smart phone, and particularly those devices that are not used for traditional office tasks like word processing and email.
I realize this is a bit vague. If you connect a monitor, keyboard, and mouse to a Raspberry Pi, it could be used like a traditional computer. But, if you make a weather monitoring station out of it and connect it to the net, I’d call it an IOT thing.
What IOT things might be on your wish list or shopping list? Smart TV’s, smart DVD players, web cameras, connected doorbells, smart thermostats, home automation equipment, connected refrigerators, connected toasters, connected coffee pots, security cameras, smart garage door openers, and so on.
Here is why you, yes YOU should care about IOT security. I do not attempt to do an in depth analysis on the subject. This is more of a brief “literature review” to pique your interest and get you to look at it in more depth.
First, credit where credit is due. This article was primarily inspired by several Security Now podcasts by Steve Gibson. I always get good stuff from him.
Security Now Web Page
https://www.grc.com/securitynow.htm
Episode 545 – Three Dumb Routers
https://twit.tv/shows/security-now/episodes/545
Episode 559 – Dumb SmartThings
https://twit.tv/shows/security-now/episodes/559
Episode 560 – Z-Wave Goodbye
https://twit.tv/shows/security-now/episodes/560
Episode 562 – IOT Infancy
https://twit.tv/shows/security-now/episodes/562
Episode 563 – IOT Infancy PT 2
https://twit.tv/shows/security-now/episodes/563
Although I’m painting with a broad brush here, suffice it to say that IOT things ABOUND with and are OVERFLOWING with security problems. This is not to say that all things have problems, but most do. These range from things like the THING has a flaw which allows someone to steal the WiFi key to your network to the THING leaks or sends your private data or habits to an insecure server to the THING can be hacked remotely and taken over, etc.
You NEED to read this book. Don’t mess around and don’t wait. Just go to Amazon and get it and read it. I don’t make any money if you do, and there’s no referral code in the link. But, it’s good info that you need to know. Most of you have NO IDEA how much danger you or your kids may be in from cyber crime and from those cool IOT things.
Future Crimes – By Marc Goodman – also in Audible and Kindle.
http://www.amazon.com/Future-Crimes-Everything-Connected-Vulnerable/dp/0385539002/
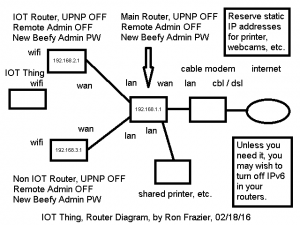
If you buy IOT things, consider connecting them to their own separate WiFi router in your home. That router should then be connected to a main router which should then be connected to your cable / dsl modem. Your Non IOT things would be connected to a third router which is also connected to the main router. Note, however, that to talk directly to your IOT thing, like a camera, you’d have to attach your phone / tablet / pc to the IOT router. If the IOT thing talks to an external service on the net, and your phone / tablet / pc talks to that service to interact with the IOT thing, there should be no problem communicating with the IOT thing.
Below is an example diagram of how you could connect your things on their own router. This helps isolate the things and minimizes damage and danger to your network if one or more things is compromised.
Below is a list of links I found that looked interesting by googling for IOT hack attack. I didn’t read every word, but scanned them for the gist of the article and for quotes. These should serve to introduce you to the issues involved. I may edit this post later with some more tips, but for now, just know that you, yes YOU should be concerned about IOT security.
You may keep up with updates to this article via the RSS feeds for the IOT category or the security category or any other category which is listed at the bottom of the article.
https://techstarship.com/category/iot/feed/
https://techstarship.com/category/security/feed/
See list of links below.
Ron
http://www.betaboston.com/news/2015/08/03/after-car-hack-internet-of-things-looks-riskier/
“hackers could remotely seize control of over a million Chrysler automobiles”
http://www.networkworld.com/article/2977094/internet-of-things/anatomy-of-an-iot-hack.html
hypothetical scenario of attack on kitchen oven leads to shut down of power grid
http://www.tripwire.com/state-of-security/security-data-protection/cyber-security/the-internet-of-things-is-here-5-connected-devices-that-can-already-be-hacked/
“between 26 and 212 BILLION devices will be connected to the web by 2020”
“5 things that can already be hacked – webcams, automobiles, refrigerators, printers, medical devices”
http://www.tripwire.com/state-of-security/security-data-protection/hacked-shopping-mall-cctv-cameras-are-launching-ddos-attacks/
“shopping mall cctv cameras are launching ddos attacks”
http://umsa-security.org/are-your-prepared-iot-is-getting-hacked/
“nearly 70% of attack victims are targeted for the purpose of advancing a different attack against another victim”
http://tech.firstpost.com/news-analysis/iot-devices-could-be-the-breeding-ground-for-hack-attacks-in-holiday-season-say-experts-288761.html
“any connected device can be a pivot point into your network”
“many people take home sensitive corporate material”
“wifi connected coffee maker … hacker can drive past your house and steal your wifi key”
“if you haven’t configured your kettle … hackers can … take over your kettle”
http://grist.org/news/hackers-can-now-mess-with-our-infrastructure-thanks-internet/
“675,186 — the number of cyber attacks against industrial control systems that occurred in January 2014”
“hackers attacked a German steel mill, causing serious damage to a blast furnace”
http://www.zdnet.com/article/samsung-connected-home-fridge-becomes-weapon-in-mitm-attacks/
“Researchers have uncovered security flaws in Samsung’s IoT smart fridge which can be exploited to run man-in-the-middle (MITM) attacks.”
http://www.baltimoresun.com/news/maryland/bs-md-hacking-internet-things-20151024-story.html
“Earlier this year, tests conducted by the Defense Department identified cybersecurity vulnerabilities in Apache helicopters, drones, Army radios and Navy ships.”
“Security cameras, drones, door locks and a home automation system were found to have vulnerabilities.”
“drone, made by a company called Parrot, has a widely known flaw that allows others to gain control of its systems”
http://about.att.com/story/cybersecurity_insights_report.html
(not IOT specific but still relevant)
“75% of Businesses Not Engaging Full Board (of directors) in Security”
“458% increase in the number of times hackers searched Internet of Things connections for vulnerabilities”
“51% of organizations are not re-evaluating their information security as a result of high-visibility data breaches”
“78% of all employees do not follow the security policies set forth by their employer”
This next one is scary.
https://www.linkedin.com/pulse/10-most-terrifying-iot-security-breaches-so-far-you-arent-montgomery
“10 IoT security breaches (so far), which you’re probably not aware of.”
“nuclear facilities, steel mills, energy grid, water supply, hospitals, building infrastructure, oil rigs, firearms, airplanes, the kitchen”
http://recode.net/2014/07/29/the-internet-of-things-is-the-hackers-new-playground/
target breach was carried out by an attack on hvac maintenance system
hp analysis – 10 most popular IOT – “found 250 different security vulnerabilities in the products”
https://securelist.com/analysis/publications/66207/iot-how-i-hacked-my-home/
“We need to understand that EVERYTHING we connect to the network might be a stepping stone for an attacker”
“After researching the network storage devices I found over 14 vulnerabilities that would allow an attacker to remotely be able to execute system commands with the highest administrative privileges”
http://arstechnica.com/security/2015/11/man-in-the-middle-attack-on-vizio-tvs-coughs-up-owners-viewing-habits/
“smart TV from Vizio that was subjected to a man-in-the-middle attack because it couldn’t be bothered to validate the HTTPS”
http://cladirect.com/en/2015/09/28/security-when-the-iot-attacks-4-examples-of-the-highest-security-stakes/
“exploits a vulnerability in the firmware of a widely-installed hotel room, opening the door”
http://www.trendmicro.com/vinfo/us/security/news/internet-of-things/fbi-warns-public-on-dangers-of-the-internet-of-things
“FBI Warns Public on Dangers of the Internet of Things”
http://embedded-computing.com/articles/understand-the-risk-associated-with-the-internet-of-things-why-would-a-hacker-attack-my-toaster/
“We’re at a crisis point now with regard to the security of embedded systems”
“In short, hackers have an incentive to create an army of malware-infected toasters.”
http://www.apexitgroup.com/blog/the-internet-of-things-might-invoke-murder-ransom-and-more
“Europol, Europe’s crime intelligence agency, believes that the Internet of Things era will be dominated by new types of hacking attacks, including the potential death”
“possible to hack into an Internet-connected insulin pump”
http://www.computerworld.com/article/2981527/cybercrime-hacking/researchers-hack-a-pacemaker-kill-a-man-nequin.html
“Researchers hack a pacemaker, kill a man(nequin)”
http://www.americanbar.org/publications/aba_health_esource/2015-2016/september/hackattack.html
“FDA issued a warning to the public regarding the security risks associated with the use of Hospira’s Symbiq infusion pumps.”
“(FBI) Deficient security measures, patching challenges and a lack of security awareness have provided cybercriminals opportunities to remotely attack these devices”
“Each attack had an immediate impact on the (telesurgery) robot, making it difficult to control and carry out the operation”
https://securityledger.com/2014/01/when-the-internet-of-things-attacks-parsing-the-iot-botnet-story/
“a spam campaign totaling 750,000 malicious emails originated with a botnet made up of “more than 100,000 everyday consumer gadgets”
http://www.bbc.com/news/technology-29643276
“Smart meters widely used in Spain can be hacked to under-report energy use, security researchers have found.”
http://www.element14.com/community/groups/internet-of-things/blog/2015/04/27/hacking-infrastructure-how-a-lack-of-iot-security-could-endanger-public-safety
“alarming security gaps in the world’s critical infrastructure organizations